As we grow into the prominence of digital landscapes, so too must any businesses looking to build into the future. With this growth also comes the evolution of cyber security needs, requiring businesses to be adequately prepared for new and shifting threats.
This is certainly the case when it comes to enterprise content management security, as breached data such as customer information, financial data, and proprietary business strategies can prove to be costly both to a company’s finances and reputation. In this article, we’ll navigate the importance of having secure content management systems (CMS), why it’s a primary concern, common risks, and how modern solutions are providing advanced security features.

The Importance of Security in Content Management
Any place that stores vast amounts of valuable data is going to be a prime target for cyber attacks. So, it’s pretty straightforward as to why every business needs to emphasize secure content management.
Why Cybersecurity is a Top Concern for CIOs
Information security is typically near the top of any CIO’s priority list. That likely isn’t changing any time soon, especially with all sorts of new threats arriving with modern technology. In fact, 97% of U.S. CIOs reported cybersecurity threats as a serious concern. For good reason, too. In 2024, researchers found that the average cost of a data breach was $4.88 million. Those same researchers, however, also found that companies using advanced security technologies to protect their sensitive data saved an estimated $2.22 million compared to those without upgraded security measures.
Beyond concerns directly related to cyberattack threats like phishing and ransomware, CIOs have other ongoing security considerations. Namely, continually changing compliance regulations (GDPR, HIPAA, etc.), as well as rising expectations around secure digital collaboration as remote work continues to expand.
Risks of Unsecured Document Management
Poor document management can open up businesses to a whole world of headaches. These risks span from overarching issues to more direct problems.
Common risks include:
- Financial impacts: As noted above, lapses in proper data management can prove extremely costly. These costs are incurred not just in lost operations but also in things such as legal fees, regulatory fines, expenses associated with damage control, and overall business value loss.
- Operational process disruptions: Breaches aren’t something you can just plug in and forget about. They are often accompanied by temporary shutdowns and potentially lengthy investigations. Until a cause is found and a recovery plan is fully complete, business operations and productivity are sure to take a hit.
- Reputational damages: Once word gets out there’s been a breach, a certain level of reputational damage is already done. Depending on the gravity of the documents that were compromised, businesses can expect some impact on trust and loyalty from customers, potential partners, and even prospective employees.
- Lost and stolen sensitive information: An obvious risk of having unsecured document management is the increased potential for crucial documents to go missing or even worse, get stolen. Without a secure CMS, documents are not only more prone to security breaches but also to human error — like getting sent to the wrong party, getting mislabeled, or simply getting missed and forgotten about. The result in all of the above situations? Reduced operational productivity and increased costs incurred.
- Difficulty in Disaster Recovery: Without secure backups and off-site storage, recovering documents in the event of a disaster becomes a more harrowing process.
- Legal consequences: In the case of exposed documents containing intellectual property or confidential customer records, legal consequences are sure to follow. Settlement fees and general legal costs swell up quickly, adding more injury to an already costly situation.
- Regulatory consequences: Piggybacking off of legal consequences and improper content management security is a one-way ticket to non-compliance with strict regulations. In addition to the resulting legal fees, failure to comply properly with established regulations often results in hefty fines as well.
When it comes to mitigating these risks, having competent content management security, and compliance systems in place is a must for any business handling valuable assets.
Advanced Content Security Features in IXIA CCMS & Xyleme
Knowing the risks of unsecured documents is one thing, but what exactly is the solution? As we’ve stated throughout this article, current developments in technology are driving businesses into the future, so it should track that any CMS integrations you adopt need to utilize advanced technologies to keep your content secure.
An overview of key security features include:
- Role-based access controls: Control access based on roles/individual input.
- End-to-end encryption: Information remains unreadable to unauthorized parties at all times, whether in transit or in storage.
- Multifactor authentication (MFA): Users attempting to access data are authenticated and confirmed to be who they claim.
- Version tracking/audit trails: Changes and access attempts can be monitored and reviewed as to what was altered, when it was altered, and who altered it.
- AI and automation adoption: Provide a new level of flexibility with fully transparent AI infrastructure documentation, including highly customizable security controls (as well as the ability to simply disable them and bypass the given infrastructure for enterprises that do not want to or cannot take advantage of such features)
MadCap’s IXIA Component Content Management System (CCMS) and Xyleme Learning Content Management System (LCMS) are two prime examples of modern systems that provide all of the above and feature SOC 2, Type II compliance — meaning they provide water-tight advanced security feature implementation. Whether you implement a CCMS, LCMS, or both, high-priority security features are paramount to safeguarding critical documentation.
Robust Access Controls and Encryption Measures
One of the first systems that should be established when implementing content management security is role-based access control (RBAC). These controls assign permissions based on specific roles and responsibilities a user has. In doing this, individuals only have access to information that requires their input, reducing the exposure of certain documents to unauthorized access or accidental modification. When implemented correctly, RBAC also allows for flexibility around reviewing and altering certain permissions as organizational roles or needs change.
To go along with RBAC, and to achieve the most robust approach, is the implementation of some form of multi-factor authentication (MFA). By pairing these together not only are documents limited to certain people/roles, but the people accessing them are also verified and authenticated, reducing the risk of a security incident.
While RBAC helps keep documents in front of the correct eyes within a company, data enterprise-grade encryption is the key feature in keeping all of your documents safe from any unauthorized parties. This encryption should be in place for data transmission and storage, ensuring that in the event of a security breach, the information within is unreadable and unusable by the compromising party.
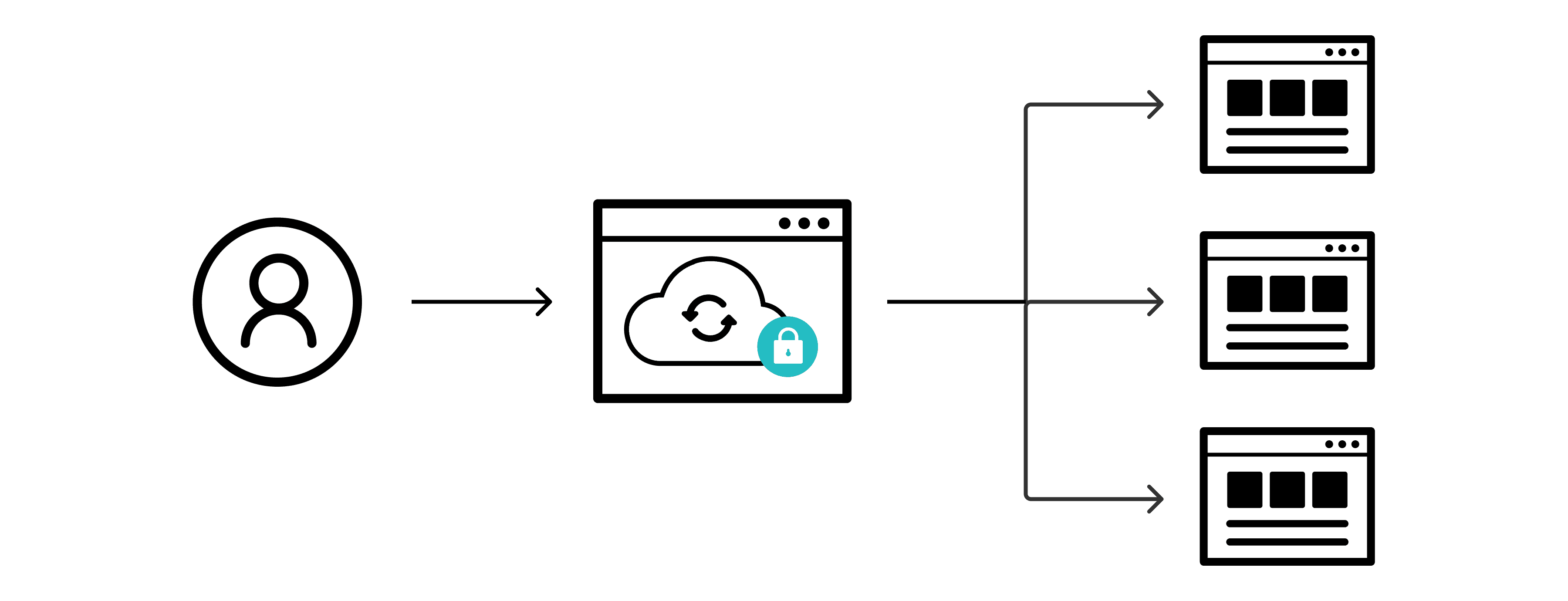
Version Tracking and Audit Trails for Full Transparency
In the case of documents with widespread access, incorrect or unwanted alterations can be a cause for serious scrambling. Modern systems solve this with version tracking and audit trails. These features can provide real-time updates as to what information was changed, when it was changed, and even who changed it.
Audit logs can also help track down suspicious behavior, providing information on any attempts at unauthorized access. By having fully integrated audit trails, you also gain valuable insight into operations that can help identify the causes of glitches and bottlenecks. It also never hurts to have a detailed history of events, especially with multiple users, as that information can be key in complying with regulatory requirements.
One of the best ways to facilitate this is through the implementation of content delivery software. This enables detailed version histories for content operations and provides complete insights for compliance and regulatory audits.
Safeguarding Sensitive Information Across Industries
Secure content management systems are a modern business necessity across all industries — whether it be finance, education, healthcare, manufacturing, or any other document-heavy area of business. Common security interests across various industries include:
- Finance: Safeguard financial reports and transaction records, as well as ensure regulatory compliance.
- Education: Secure access to academic and administrative documents.
- Healthcare: Secure handling of patient records and regulatory compliance with HIPAA.
Manufacturing: Safeguard specifications, designs, and other forms of intellectual property.

Building a Secure Content Management Strategy
When it comes to a robust and secure content management strategy, you’re going to want a system that provides top-of-the-line functionality and security throughout the whole lifecycle of any given document. That includes having features in place that safeguard your documents not only while they’re active but also while they’re being stored or even in the event of a security breach.
Having a blanket level of security is important when attempting to enable seamless collaboration across teams consisting of authors, developers, analysts, and data scientists — as the more interconnectivity you have, the more important content management (and by default, security) becomes. It also helps to have a single source for all your content and assets, as it reduces the number of gaps in which documents and data can slip through or get lost. A robust content collaboration software and content authoring software can help you achieve this goal by providing a secure, centralized platform for all your content needs.
If all this sounds a bit overwhelming, the answer is finding the right help. That means a one-stop shop for every aspect of your content management, including authoring, collaborating, delivery, analytics, and of course, security. With MadCap Software, your business is adopting industry-leading solutions that not only put you at the forefront of current technologies, but also help evolve your content strategies for the future. Learn more, and see how your needs can be met with MadCap.